What is Vinci Logic?
Vinci Logic is an AI-driven security operations platform that helps organizations build an autonomous SOC using detection and response as code. Based on an open XDR architecture, it lets security teams define how alerts are detected, qualified, investigated, and resolved.
Customizable Response Workflows
Customize automated security responses for any alert type, from notifications to blocking threats and disabling compromised accounts.
Built-in Automation & AI
Reduces analyst workload by letting Vinci Logic AI SOC Agent automate security response workflows.
Why Choose Vinci Logic?
Automate and Simplify Threat Detection
With built-in SOAR capabilities, Vinci Logic reduces analyst workload by automating alerts triage, and threat response.
Employs Large Language Models (LLMs) to transform disparate security signals into cohesive attack narratives and comprehensive summaries.
Empowering SOC Teams with an Advanced AI SOC Agent
Hey explain this alert to me
[2026-01-14 23:05:30]
Suspicious PowerShell Execution on Host WIN-02
🧠 AvicennAI Insight:
User jane.doe executed an obfuscated PowerShell script that attempted to access LSASS memory — a technique often used for credential dumping. The process was initiated shortly after an unusual login from an external IP (89.45.22.101).
📄 Reasoning:
The script matches patterns observed in previous Mimikatz-based attacks. This activity aligns with MITRE ATT&CK technique T1003.001. Notably, the same user was active on two additional hosts within a 15-minute window, indicating possible lateral movement.
✅ Suggested Action:
Isolate the host to prevent further spread, suspend the user account, and initiate a credential reset. Review other endpoints for similar activity.
Introducing AvicennAI, an AI-powered SOC agent that manages the full lifecycle of security alerts.
An AI-powered SOC agent that orchestrates alert handling, helping security teams understand and efficiently manage incidents while streamlining operations.
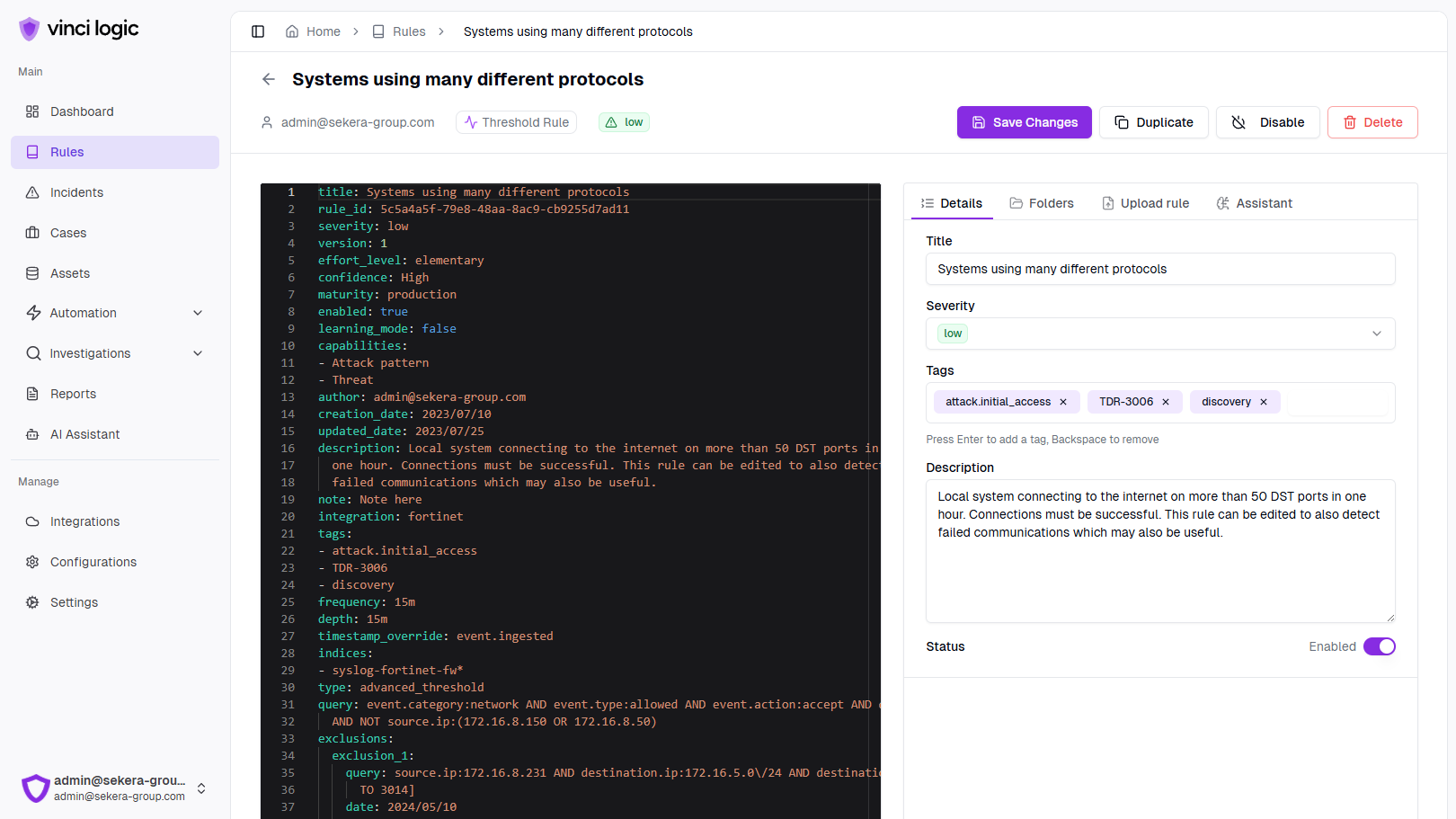
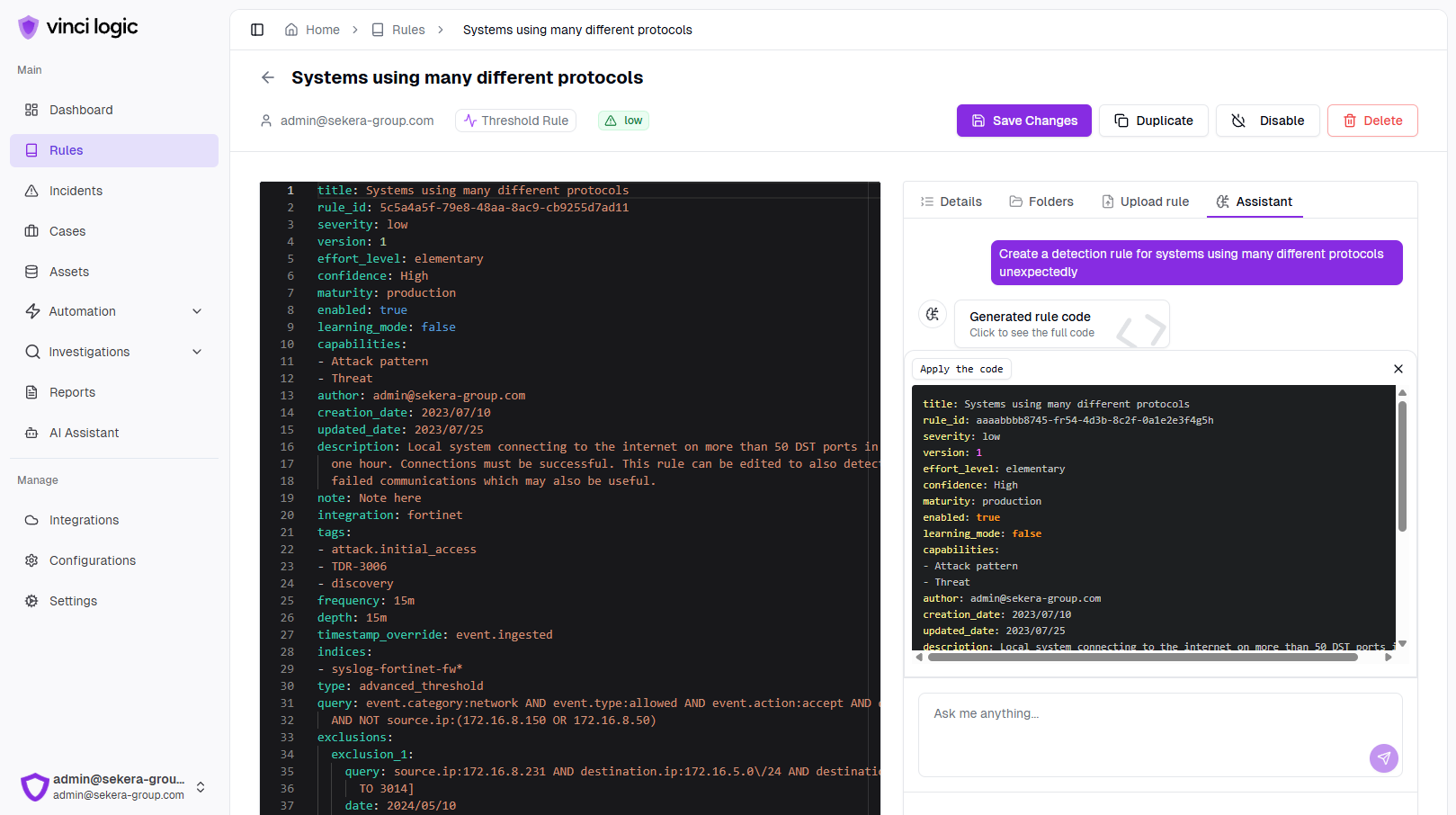
Generate a rule to detect PowerShell execution with encoded commands
title: PowerShell Encoded Command Executionid: z8koxistatus: experimentaldescription: Detects suspicious PowerShell execution patterns that may indicate malicious activity, such as encoded commands or attempts to access sensitive system processes.date: 2025/04/11references:- https://attack.mitre.org/logsource:category: process_creationproduct: windowsdetection:selection:CommandLine|contains:- 'powershell.exe -enc'- 'cmd.exe /c'- 'rundll32.exe'- 'regsvr32.exe'ParentImage|endswith:- '\explorer.exe'- '\services.exe'condition: selectionfalsepositives:- Legitimate administrative activities- Authorized system operationslevel: hightags:- attack.execution- attack.t1059
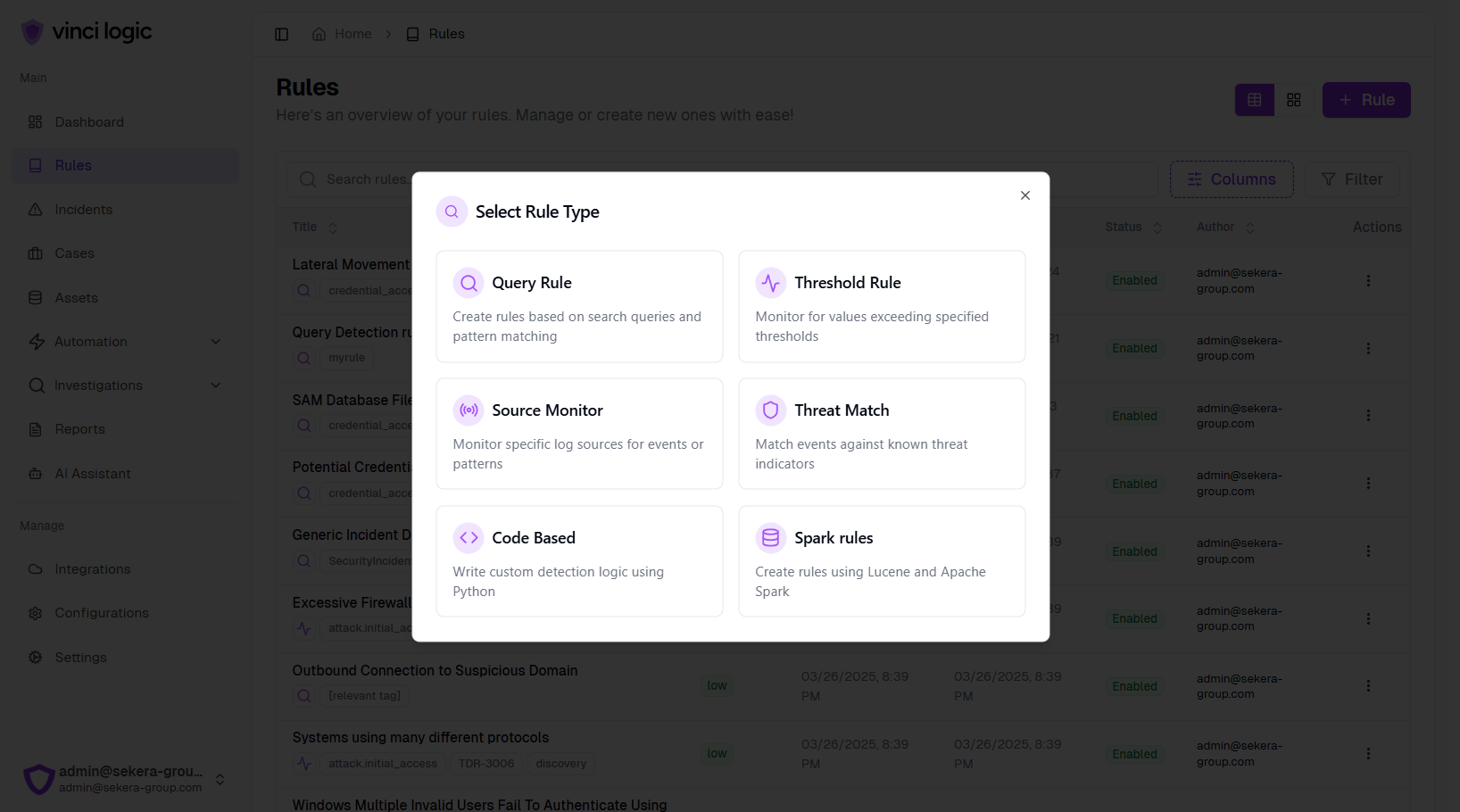
Vibe Detection and Response Engineering
AI-powered assistant helps security teams quickly craft optimized detection rules and response workflows for comprehensive threat coverage.
Flexible, Scalable and Cost-Effective Security Data Lake
Offers versatile deployment to meet diverse security needs—whether as a standalone SIEM or integrated with existing data lakes.
With native support for OpenSearch, ClickHouse, and other modern backends, it enables detection where the data lives—optimizing infrastructure, reducing costs, and breaking free from traditional SIEM vendor lock-in.
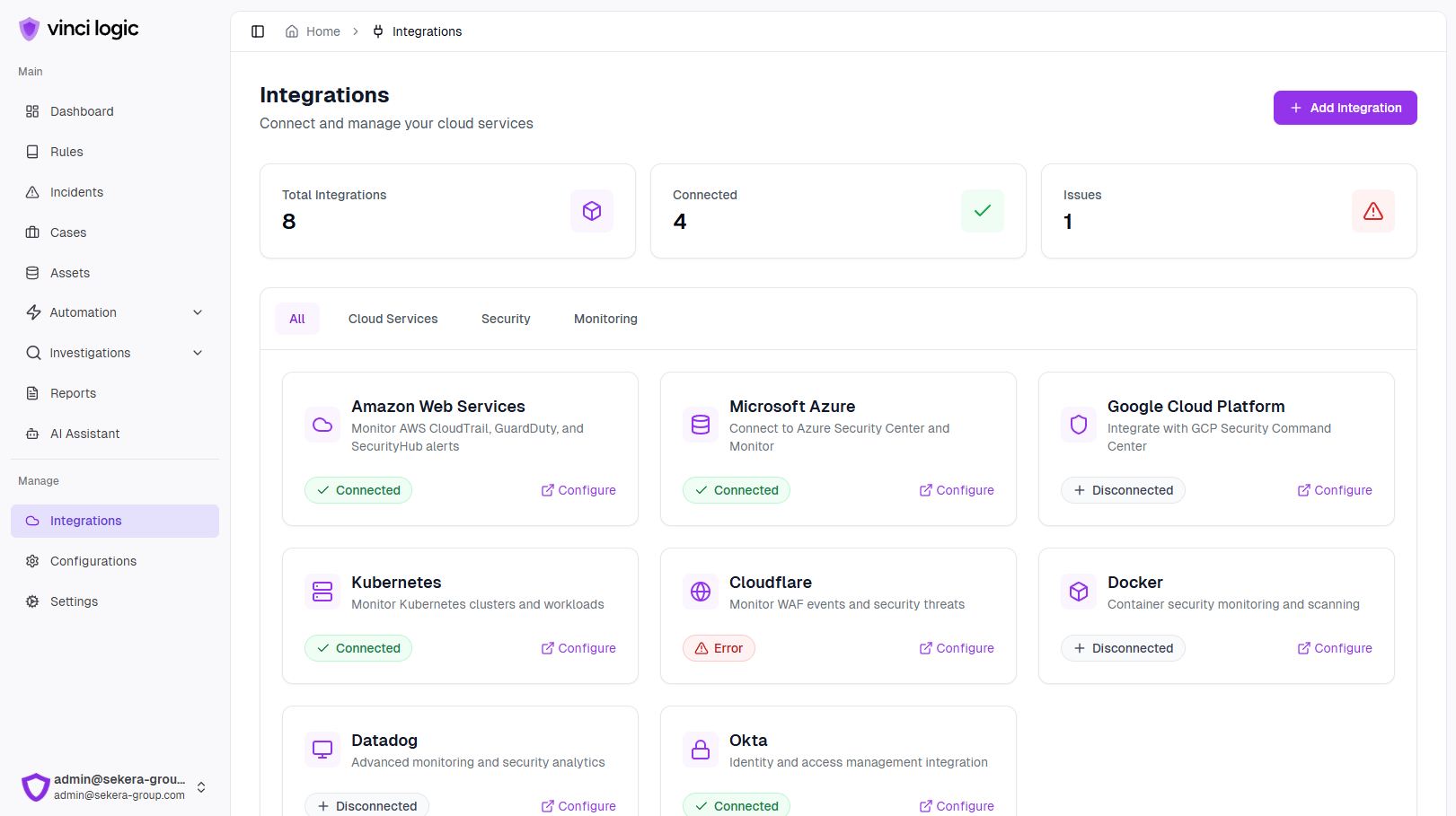
Comprehensive Security Integration
Seamless integration with log collectors, operational tools, automation connectors, and cloud infrastructures.
Continuously evolving detection content ensures adaptability to emerging threats and modern security challenges.
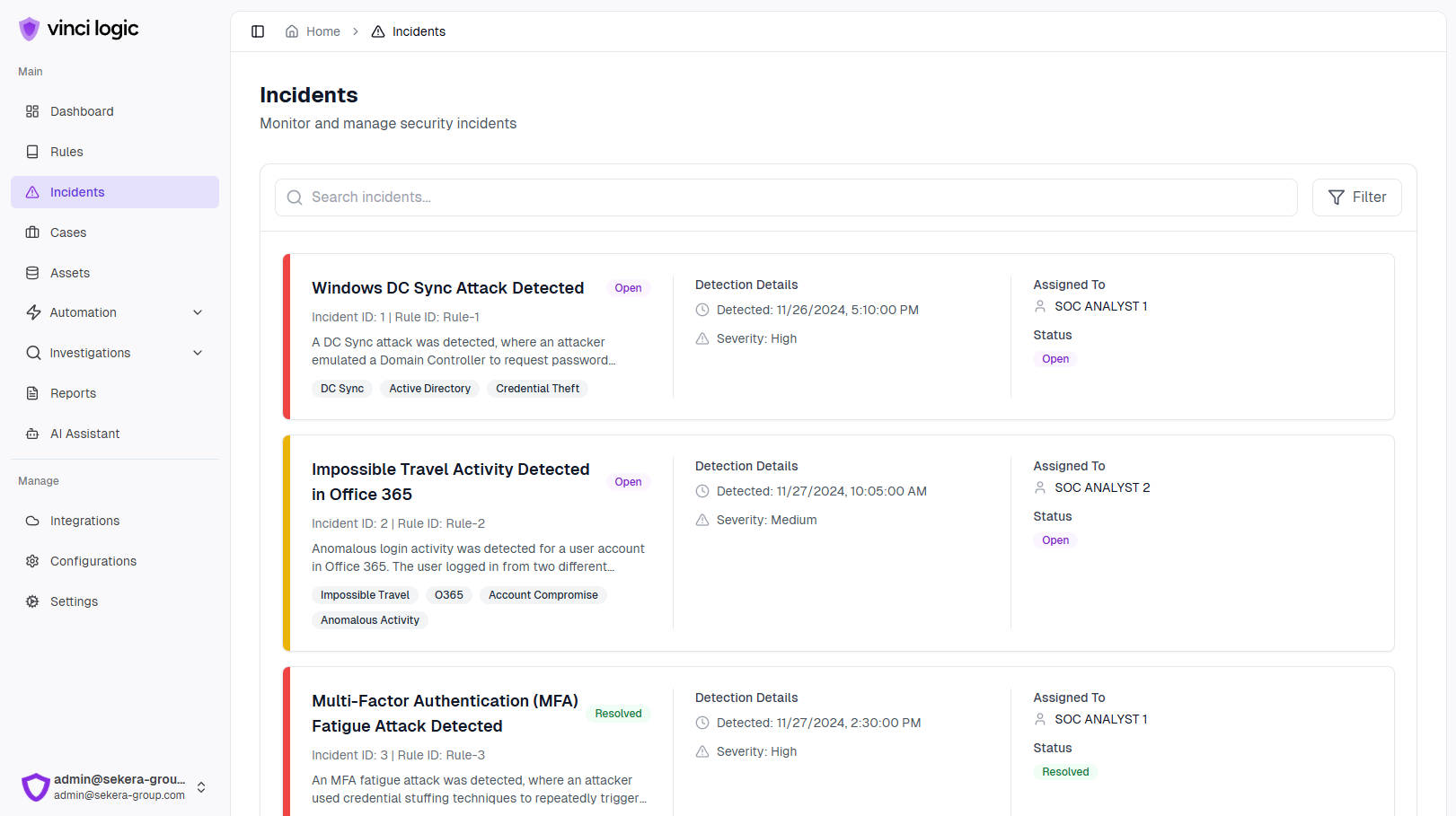
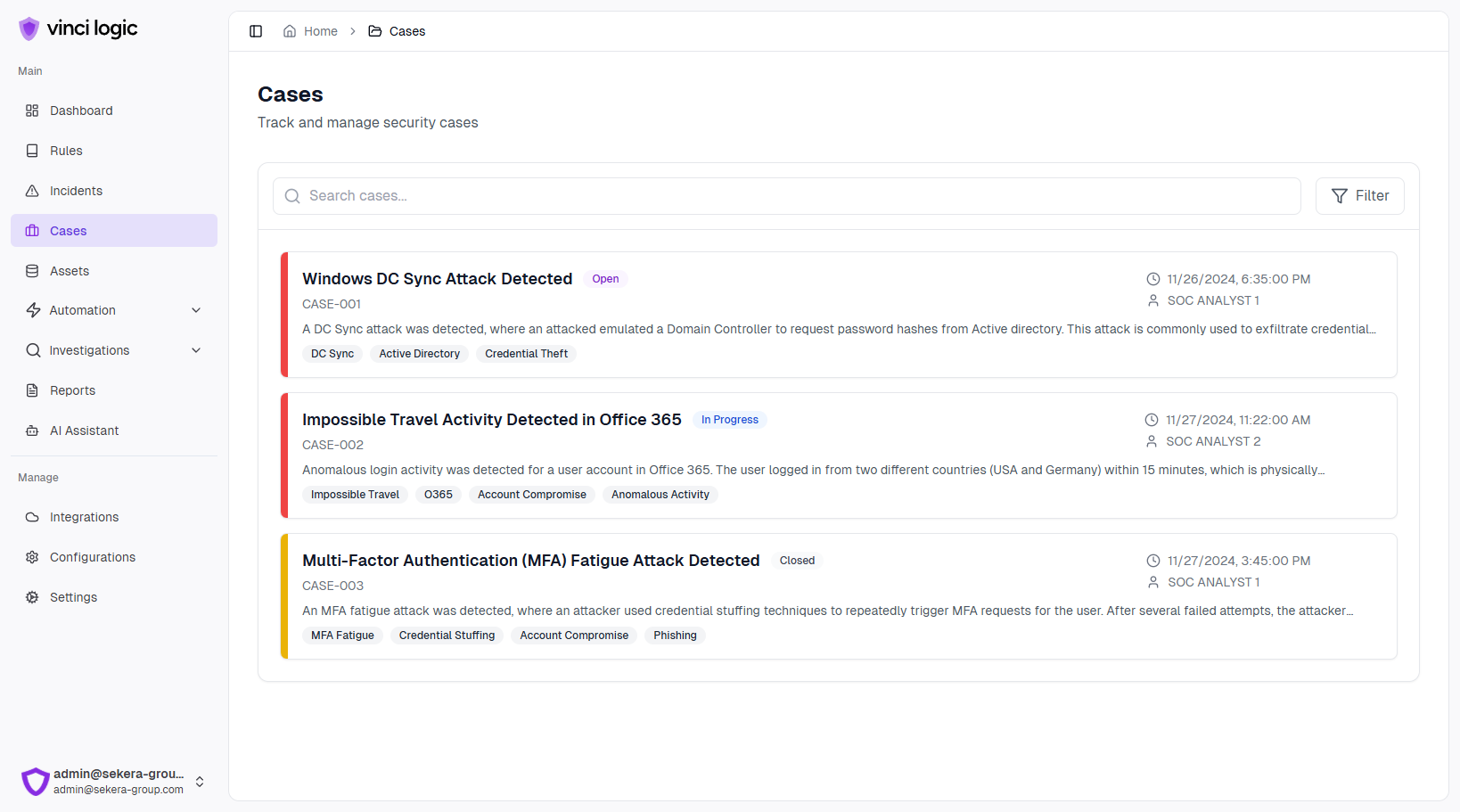
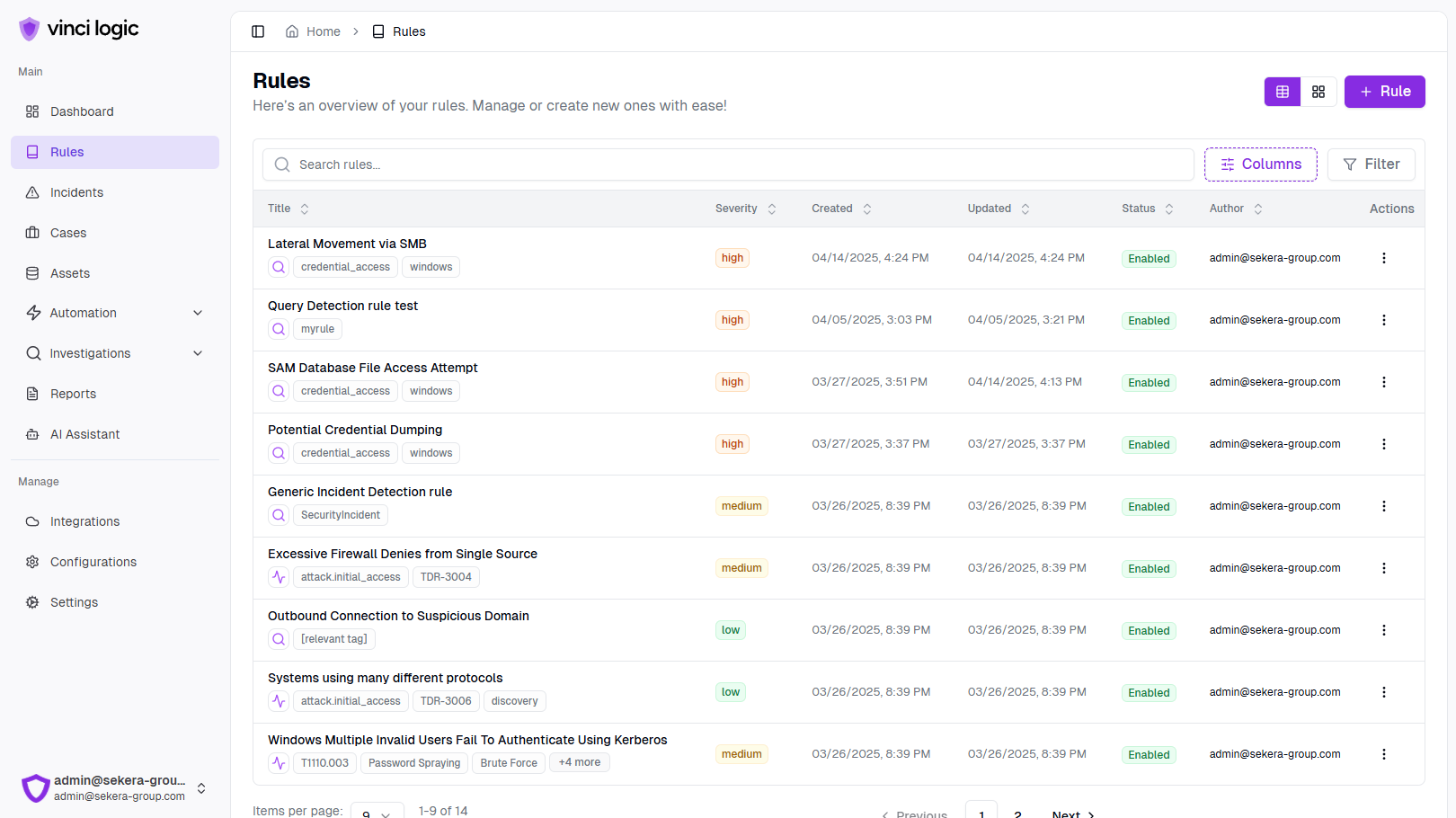
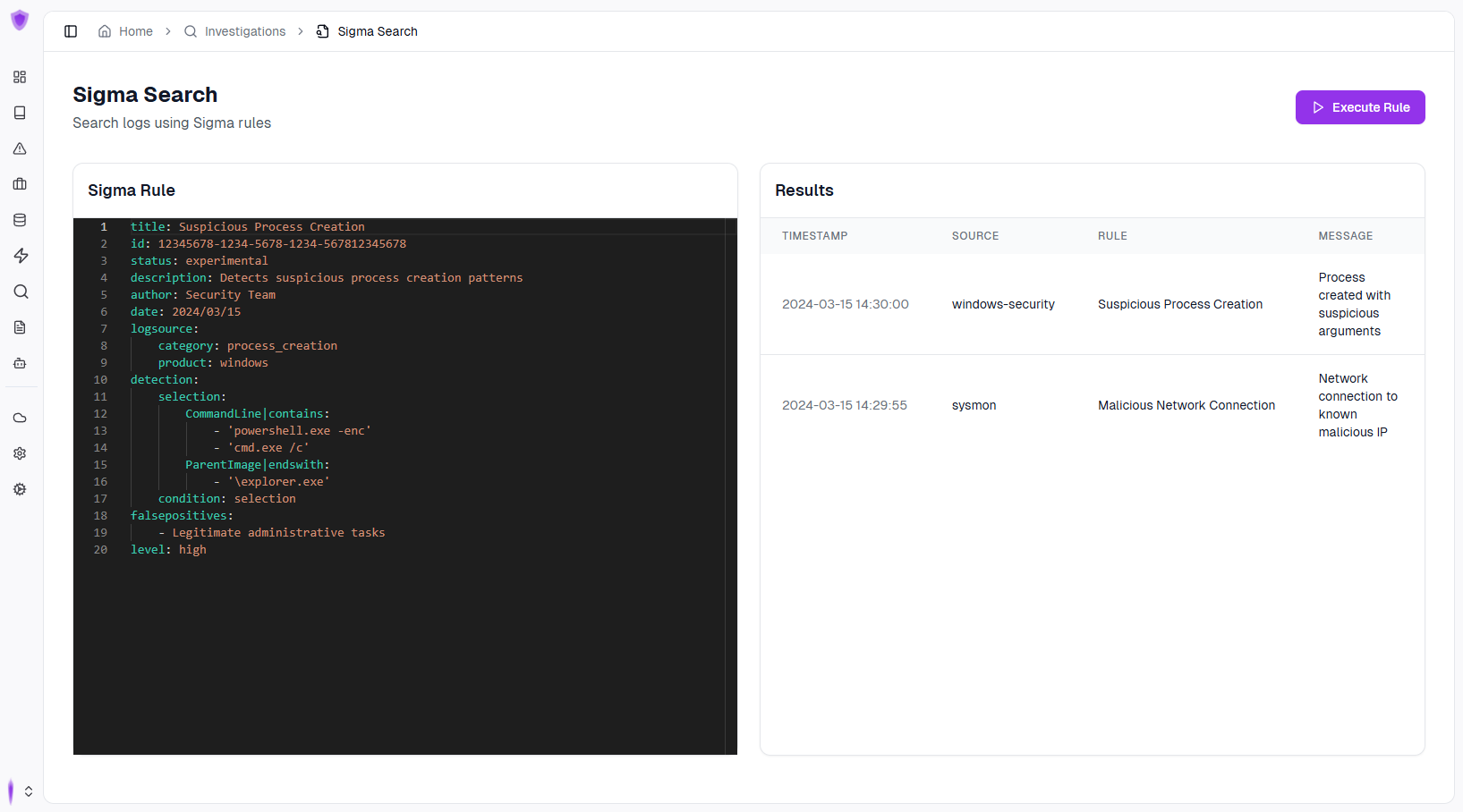
Platform Overview
Discover how our intuitive interface and powerful features work together to enhance your security operations.
Unified Security Solutions for SecOps Efficiency and CISO Cost Management
Centralize data to meet regulatory requirements.
Simplify audits with secure and organized data management.
Clear visibility into incident detection and response.
Better security management and strategic decision-making.
Reduce costs by unifying SOAR and SIEM capabilities.
Leverage scalable data storage solutions.
Harmonize Detection and Response
Decoupled SIEM and SOAR solutions lead to ineffective operations.
Centralize detection and response definitions within Vinci Logic.
A unified platform that reduces costs and enhances automation capabilities.